Security vulnerability found in Cyberoam DPI devices (CVE-2012-3372)

Last week, a user in Jordan reported seeing a fake certificate for torproject.org. The user did not report any errors when browsing to sites such as Gmail, Facebook, and Twitter, which suggests that this was a targeted attack. The certificate was issued by a company called Cyberoam. We first believed that this incident was similar to that of Comodo and DigiNotar, and that Cyberoam had been tricked to issue a fake certificate for our website.
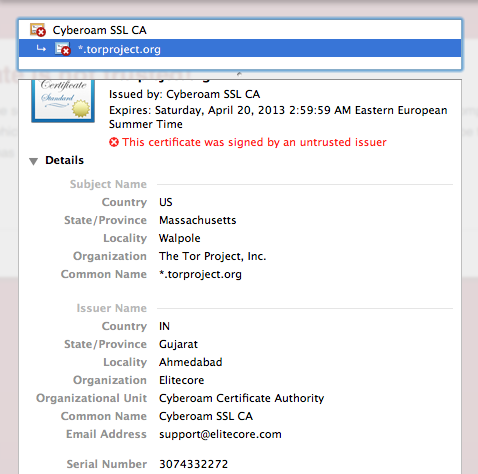
After a bit of research, we learned that Cyberoam make a range of devices used for Deep Packet Inspection (DPI). The user was not just seeing a fake certificate for torproject.org, his connection was actually being intercepted by one of their devices. While investigating this further, Ben Laurie and I found a security vulnerability affecting all Cyberoam DPI devices.
Examination of a certificate chain generated by a Cyberoam DPI device shows that all such devices share the same CA certificate and hence the same private key. It is therefore possible to intercept traffic from any victim of a Cyberoam device with any other Cyberoam device - or to extract the key from the device and import it into other DPI devices, and use those for interception.
Ben and I wrote a security advisory and notified Cyberoam of this vulnerability at 17:00 UTC on Saturday, June 30. We made it clear that we intended to publish this blog post and the security advisory on Tuesday, July 3, and encouraged them to respond promptly if they had any comments. At the same time, we notified browser vendors and asked that they blacklist the Cyberoam CA certificate in their browsers.
Cyberoam have not yet commented on this issue, apart from acknowledging our first email and saying that they are looking into it. The Cyberoam CA certificate is not trusted, and so browsers will show users a warning (unless someone has already installed the certificate). Users with the Tor Browser Bundle are not affected.
To check if this CA is installed in your browser, see the following instructions for Internet Explorer, Firefox, Chrome, and Safari. The instructions mention DigiNotar, but they are still valid. If you have more information about this issue, please email help@rt.torproject.org.
Comments
Please note that the comment area below has been archived.
BoingBoing is reporting this
BoingBoing is reporting this as a "mass surveillance device," but Cyberoam makes consumer/SMB UTM appliances which do SSL inspection by generating their own certs, via a mechanism similar to that used by other vendors (Fortinet, SonicWALL, Palo Alto Networks, etc.)--a mechanism which won't work with DNSSEC and DANE.
As I understand it, DNSSEC
As I understand it, DNSSEC doesn't protect the confidentiality of data being transmitted between a Web browser and its intended destination, DNSSEC merely ensures that DNS isn't being tainted or otherwise modified. It's SSL, or TLS as it's often ascribed, which does it; but SSL uses a MAC to ensure that the integrity of transmitted data remains intact or unaltered as it is. But it doesn't prevent these devices from does as they're intended; neither will DNSSEC if I'm not otherwise mistaken. It should be said that SSL itself isn't at fault. But should I trust CAs anymore? Or if I create a CA myself, should I trust myself any more than I trust a CA?
The DANE part was the
The DANE part was the important one... http://datatracker.ietf.org/doc/draft-ietf-dane-protocol/
I thought that I'd confused
I thought that I'd confused myself, at least I now know that I've confused myself. Thank you; I'll browse it whenever I've an opportunity to! But I presume that SSL does use a MAC nonetheless? Or is it TCP/IP which ensures integrity of data either transmitted or received?
wut
wut
Any router that does SSL
Any router that does SSL inspection is, by definition, a mass surveillance device.
Yes, I understand it but
Yes, I understand it but does it not upon whether or not said surveillance is subject to consent or not? Would it not be proportionate or proper that these devices could be used to deter or detect suspected industrial espionage? Would I be being inappropriate or improper if I didn't condone use of these devices for the aforementioned purposes?
I'd interpret SSL inspection
I'd interpret SSL inspection by an organization on its own user traffic to NOT be "mass surveillance." "Mass" seems to connote, as has been noted, a broader level of interception without consent. It has been claimed here, without evidence, that the Cyberoam was at the user's ISP rather than, say, the company he works for. If that is shown to be the case, I'll reconsider.
Without evidence? Did you
Without evidence? Did you miss the screenshot above?
It would be useful if the
It would be useful if the specific public key certificate being discussed could be made available to allow those affected to ensure that they're either able to identify and delete or distrust Cyberoam's CA public key certificate as appropriate. But that being said, it's rather shrewd of Cyberoam to believe that their CA public key certificate would be accepted as-is, is it not?
Regarding your incorrect
Regarding your incorrect statement
"The certificate was issued by a US company called Cyberoam.":
Understandably you were scrambling to straighten out this mess that hit torproject and thank you for that.
To clarify for others, the cert you show above shows and the company's website confirms that Cyberoam is an Indian company (with a US branch). Its world headquarters is in India. The certificate shown specifies Gujarat in Ahmedabad as the location. Even the time zone of the certificate's stated expiration is Indian.
I was under the impression
I was under the impression that Cyberoam was a US company with an Indian branch, but I'll look into it. Thanks!
Is Cyberoam participating in
Is Cyberoam participating in discussion whatsoever, or is it refusing to publish a comment or statement?
Or it is a proxy attack
Or it is a proxy attack through the bought in subsidiaries of an U.S. business.
Screenshot says:
Organization: ELITECORE
Email Address: support@elitecore.com
Registrant:
Elitecore Technologies PLC
10 Schalks Crossing Road
Suite 501-329
Plainsboro, NJ 08536
US
ELITECORE.COM:
Technical Contact of ELITECORE.COM:
Patel, Hemal hemal@ECLIPSEMICRO.COM
9 Nicola Ct
Cranbury, NJ 08512
US
201-422-9200 fax: 201-735-5888
ECLIPSEMICRO.COM:
Administrative Contact of ECLIPSEMICRO.COM:
Patel, Hemal hemal@ECLIPSEMICRO.COM
9 Nicola Ct
Cranbury, NJ 08512
US
201-422-9200 fax: 201-735-5888
About ECLIPSEMICRO.COM:
"Eclipse Micro Computer was founded in 1993. Our annual growth is derived from clients throughout the United States, the Caribbean, Europe and Asia. It is our commitment and dedication in understanding our client’s needs that has enabled us this growth. As a Certified Minority Business we are committed to the highest quality and customer satisfaction.
With the opening of foreign economies, we took our first step by establishing joint ventures in developing countries. We formed a Joint Venture (JV) with Eleclipse Network Pvt Ltd in India to start an Internet Service Provider (ISP), under the trade name IceNet, Net, India. This experience has expanded both our services and our technological knowledge. Today IceNet is one of India’s largest ISPs utilizing Fiber Optic technology.
In further expanding our presence in Asia, we Joint Ventured with Elitecore Technologies Ltd, India to provide a software development center specializing in JISP, JHotline, Cyberoam, Elite Web Mail, and services for Web Based Application Development, Networking Solutions, Atomization and Process Engineering, E-commerce Applications, etc. Complementing our US capabilities.
With the Hispanic market's rapid growth, we started an Internet Service Provider (ISP) in Puerto Rico, under the trade name ICENetworks.com, Inc.This ISP is quickly growing and will soon be the largest ISP in Puerto Rico.
Through out the world, our highly skilled staff is devoted to supporting the client server needs of the business community. Eclipse specialties include the design, testing and implementation of major client/server infrastructures that allow clients to reduce system administration costs through the design and implementation of uniform models."
Guajarat, India, hosts the servers of icenet.net.
Cyberoam s a division of
Cyberoam s a division of Elitecore Technologies. Elitecore has offices in USA, Middle East & India and has its R&D and Global Support Management Centre in India. It seems the main HQ is in India.
To clarify for others, the
To clarify for others, the cert you show above shows and the company's website confirms that Cyberoam is an Indian company (with a US branch).
Are you serious? Cert proves nothing, for your clarify. You need to point and to cite parts of the company's website that confirms that Cyberoam is an Indian company.
To add to Eclipse Micro
To add to Eclipse Micro Computer Inc - Cyberoam connection.
Eclipse Micro says about its Elitecore Technologies Pvt Ltd venture:
"With aim to provide and extend the ISP Technological Expertise, we ventured into Elitecore, now the backbone for many ISP’s in India. With an In-House team of 50 professionals, Elitecore has conceived and Developed Software products like JISP, JHotline, CYBEROAM and Elite Web Mail for Internet Enabled Services."
As far as expiration time:
As far as expiration time: it is not Indian, it Easter European Summer Time
Thanks to the god, I'm
Thanks to the god, I'm always using a Tor bundle!!! XD
Ok I changed the certificate
Ok I changed the certificate to not trusted like the instructions said. I decided to take it to the next level and delete it all together. The problem is it will not delete!! Any ideas I am using an OSX 10.5
I suspect that if you've
I suspect that if you've decided to distrust it just now, in the meantime it shouldn't be a concern as your Web browser will not trust either Cyberoam's CA public key certificate, nor others that it has issued.
http://www.jirasekonsecurity.
http://www.jirasekonsecurity.com/2011/09/how-to-disable-diginotar-root-…
I marked the certificate as
I marked the certificate as untrusted, but when I went to diginotar.com to verify everything was cool, the page wouldnt open. Is this a good thing. The instructions said I needed to make sure it said "Safari can not verify..."
ckcckkc :D :::
ckcckkc :D :::
"but they are still valid"
"but they are still valid" isn't really accurate. The Chrome instructions are outdated.
How to visit torproject.org
How to visit torproject.org without anyone being able to intercept?
Deleting a root CA
Deleting a root CA certificate from Windows is not good enough. Unless you specifically stop it, Windows will silently go to the Internet and try to download a root certificate that it thinks it needs and installs it without prompting.
http://netsekure.org/2011/04/automatic-ca-root-certificate-updates-on-w…
What?! Would it be
What?! Would it be preferable to distrust it or otherwise disable it as opposed to attempting to delete it in the meantime? If Microsoft Root Certificate Program is defined by Microsoft, is it not incumbent upon Microsoft to ensure that Cyberoam's CA public key certificates couldn't be installed whatsoever? Would it be possible to do it, or could Cyberoam merely create another and thus render it useless?
Cyberoam ships a lot of
Cyberoam ships a lot of private keys in firmware updates.
Decrypt updates with this key:
-----BEGIN RSA PRIVATE KEY-----
MIICXgIBAAKBgQC554Ro+VH0dJONqljPBW+C72MDNGNy9eXnzejXrczsHs3Pc92V
aat6CpIEEGueyG29xagb1o7Gj2KRgpVYcmdx6tHd2JkFW5BcFVfWXL42PV4rf9zi
Yon8jWsbK2aE+L6hCtcbxdbHOGZdSIWZJwc/1Vs70S/7ImW+Zds8YEFiAwIDAQAB
AoGBAKTvnFGKSkUJnNQGe66I0wunGgCA3W7kbarAzEF2qKYhGlZhJQnn68RmVnAW
pXUFvB+vmtu/+4J9OmWBJsGHFvC9xH32a0PWNr7APjAKrjAD8GWS7Z6BjuxN8QhD
WlFMmpYhYIjT1jt7RNfs2gJGS2Ryu3zutUQGwtUB9Pou03dJAkEA6yttwVINFqQP
utgUZ1JUHrN/rE73FzYsF/CwJp5d3rLHenZzLT0iW+kNDLUw/VpzYxK7bF2Qrt/3
QIUWwm2InQJBAMpe+jhNMJeLDLc3tG3zeithT0mFkuzWWmT2PJgQ0V78UWhw/fSn
Qqnq7KBY/DNjlfhezrozLDD73/ccmha0Ax8CQQCBaBlyOtNm9QqO116K6HvPlRiZ
Wa6QQEgNOG3GInknFZu9ILcKWsywZNLAfmgh0gcSqnkmDWqTQD0PbOz0Ok/lAkEA
g24JrfUbwOASww9PhDUju/a36rTwhhZ0oKt3EP+jKsBOErmHhZP3bKlhQoZoTOu5
Y5QXSMChS7LZcwDFZkdE2wJATRgMbhErif+ZRwt9XJRdCo5Sx6ewyGyxjc5gvUyK
KegHcgru/ZC3pGlujRD2LqxgJNAn5QTdW4LK8xVPFySTYg==
-----END RSA PRIVATE KEY-----
OpenVPN configuration and keys:
port 8443
mode server
tls-server
proto tcp-server
dev tun
topology subnet
port-share 127.0.0.1 4128
dh /usr/local/sslvpn/keys/dh1024.pem
ca /usr/local/sslvpn/keys/FactoryDefault.pem
cert /usr/local/sslvpn/keys/FactoryCert.pem
key /usr/local/sslvpn/keys/FactoryKey.key
ifconfig 10.81.234.5 255.255.255.0
push "topology subnet"
comp-lzo
persist-key
persist-tun
verb 1
status-version 2
keepalive 60 300
/usr/local/sslvpn/keys/dh1024.pem
-----BEGIN DH PARAMETERS-----
MIGHAoGBAMqcURr/SGr2qctu5ZLvB9xjSjji1WSVxiUZ3jKerrKy/9QjG/vFP8JY
3TE6/NXOMs6iWz8A2tLIzhW0um66MMjngV1JXaFv6VoxtHmL799q/0aTa/ep0zHx
8rlCQQEI3hIj9eyfZjjjpPSYAnIbNVQ3rJy8W3XgUOGWRB2EYmobAgEC
-----END DH PARAMETERS-----
/usr/local/sslvpn/keys/FactoryDefault.pem
-----BEGIN CERTIFICATE-----
MIIEfDCCA2SgAwIBAgIBADANBgkqhkiG9w0BAQQFADCBijELMAkGA1UEBhMCSU4x
EDAOBgNVBAgTB2d1amFyYXQxEjAQBgNVBAcTCUFobWVkYWJhZDESMBAGA1UEChMJ
ZWxpdGVjb3JlMREwDwYDVQQLEwhjeWJlcm9hbTEMMAoGA1UEAxMDampwMSAwHgYJ
KoZIhvcNAQkBFhFqanBAZWxpdGVjb3JlLmNvbTAeFw0wOTAxMzEwNzA0NThaFw0z
NjEyMzAwNzA0NThaMIGKMQswCQYDVQQGEwJJTjEQMA4GA1UECBMHZ3VqYXJhdDES
MBAGA1UEBxMJQWhtZWRhYmFkMRIwEAYDVQQKEwllbGl0ZWNvcmUxETAPBgNVBAsT
CGN5YmVyb2FtMQwwCgYDVQQDEwNqanAxIDAeBgkqhkiG9w0BCQEWEWpqcEBlbGl0
ZWNvcmUuY29tMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAyU1pl4ru
v9HdxrWkScFgIDcNOBlopgwo3jNon1AUmGeGfeo2JnLnSxWAqGD8Wyw7G1t8ls3W
VIKQMmW6xwOHwWJyifZmAfKpA7TeMwVFHw48xRJIDp4rqoEIxqxv3cVxQXFDZ6Qq
Ef3bEv9+UoB27AUXfd3lvLIEyDO1y41gLtADZLe3SVlkEdscAMvijq/f1hlT4Zj0
8QEHl4vIZ/pu2S1E7X4ooDswkaxS5/5qOm2P+L7NVlxch/VRwh+Y106T1k4qDW2D
1oeIoOxexZACy+97yaSSZMQD1IG6Y807JQylCuGzowtvCFxpCwGppZRDbtPwmOPN
BBfwclNdF9ThhwIDAQABo4HqMIHnMB0GA1UdDgQWBBQGGwwgsdygDwV2jqWg5v/w
o3iHATCBtwYDVR0jBIGvMIGsgBQGGwwgsdygDwV2jqWg5v/wo3iHAaGBkKSBjTCB
ijELMAkGA1UEBhMCSU4xEDAOBgNVBAgTB2d1amFyYXQxEjAQBgNVBAcTCUFobWVk
YWJhZDESMBAGA1UEChMJZWxpdGVjb3JlMREwDwYDVQQLEwhjeWJlcm9hbTEMMAoG
A1UEAxMDampwMSAwHgYJKoZIhvcNAQkBFhFqanBAZWxpdGVjb3JlLmNvbYIBADAM
BgNVHRMEBTADAQH/MA0GCSqGSIb3DQEBBAUAA4IBAQAE/CtvgYO8/quyFlusqI5U
UKoPkiIw3K452GcD414db7s0tBdv2p6HRFDsTwglRWHqztEL3qH8oznFvz/tZ/e/
zNkhXyNqqWkJTmFe3fIL4zQPwLgkHb4PSKSuX88NfAKfe7cT3kUHg9+O5UoP4nGo
1iqwlTP3dpJnG8NjaaAsI5OIYSU7TIAQCMw08Fre25R9WcfjUxZB4IqM+Zqq0KML
ublzZjvSH0upgcRVuN2kyJVCnKCIS9xxhlklB10P+C4WxWFBqKRMHj3hYMtGO4Cp
iqOIvcpaFTf0VXlsxg2xaRvkxDNmc74Fq1az23rZpApl1vG+YV6CFK3cIM/5Xicl
-----END CERTIFICATE-----
/usr/local/sslvpn/keys/FactoryCert.pem
-----BEGIN CERTIFICATE-----
MIIEVzCCAz+gAwIBAgIBATANBgkqhkiG9w0BAQQFADCBijELMAkGA1UEBhMCSU4x
EDAOBgNVBAgTB2d1amFyYXQxEjAQBgNVBAcTCUFobWVkYWJhZDESMBAGA1UEChMJ
ZWxpdGVjb3JlMREwDwYDVQQLEwhjeWJlcm9hbTEMMAoGA1UEAxMDampwMSAwHgYJ
KoZIhvcNAQkBFhFqanBAZWxpdGVjb3JlLmNvbTAeFw0wOTAxMzEwNzA2MzhaFw0w
OTAyMTIwNzA2MzhaMIGWMQswCQYDVQQGEwJJTjEQMA4GA1UECBMHZ3VqYXJhdDES
MBAGA1UEBxMJQWhtZWRhYmFkMRIwEAYDVQQKEwllbGl0ZWNvcmUxETAPBgNVBAsT
CGN5YmVyb2FtMRgwFgYDVQQDEw9lbGl0ZWNvcmVzc2x2cG4xIDAeBgkqhkiG9w0B
CQEWEWpqcEBlbGl0ZWNvcmUuY29tMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKB
gQDKgc5DG+TwiFTv0RQMzcBxR2Eid6bAZjrZHJ9VtGrA5NuDv2M0ycfiOsxxJSWQ
djoPr+CwQolajZdYk87A82pZY6HKiU2PVXirptsE7AYH7S9M1rtZW+Edjr4V/c+U
PgNgkX6dKS2OKrx32fx3Edq4dBjKd95NlVUcj/hO3XquwwIDAQABo4IBPDCCATgw
CQYDVR0TBAIwADAsBglghkgBhvhCAQ0EHxYdT3BlblNTTCBHZW5lcmF0ZWQgQ2Vy
dGlmaWNhdGUwHQYDVR0OBBYEFEgSOGaZEGohNm0Bn58WWGFSZ3FAMIG3BgNVHSME
ga8wgayAFAYbDCCx3KAPBXaOpaDm//CjeIcBoYGQpIGNMIGKMQswCQYDVQQGEwJJ
TjEQMA4GA1UECBMHZ3VqYXJhdDESMBAGA1UEBxMJQWhtZWRhYmFkMRIwEAYDVQQK
EwllbGl0ZWNvcmUxETAPBgNVBAsTCGN5YmVyb2FtMQwwCgYDVQQDEwNqanAxIDAe
BgkqhkiG9w0BCQEWEWpqcEBlbGl0ZWNvcmUuY29tggEAMCQGA1UdEQQdMBuBGWph
bHBhLnBhdGVsQGVsaXRlY29yZS5jb20wDQYJKoZIhvcNAQEEBQADggEBADGvwvhD
w96cdy+JV2dL5iphpYh0RHVFkqKSPDukY7TdIP3scjcCAayrqsW9JmX1SR0iRYRN
2r1360Q1g9o262Tmx2MMWZ+qVkpMNYzDMr22qurYlMss8ZhR8Llk8IiAM+PAVwY7
OwjTDweFauLv+H/Mqt8FF1yvxQMHcQtE1GyHDTjNb2NMr9siRACSwzPvUnJKUL8X
vdyqk2LEC+MIR7+xTCfCXx0sFVwTrvyZAoFgbH/DKn1hUdRwXwLI0zUuzJnMzlnR
VrpjCmFvntL+wWGIXK3q4uG2jBeGlEtiMdbXUVVGLGItE/DhS15vPJG5yWOA/Z17
gL4XzxM79IC2dAc=
-----END CERTIFICATE-----
/usr/local/sslvpn/keys/FactoryKey.key
-----BEGIN RSA PRIVATE KEY-----
MIICXAIBAAKBgQDKgc5DG+TwiFTv0RQMzcBxR2Eid6bAZjrZHJ9VtGrA5NuDv2M0
ycfiOsxxJSWQdjoPr+CwQolajZdYk87A82pZY6HKiU2PVXirptsE7AYH7S9M1rtZ
W+Edjr4V/c+UPgNgkX6dKS2OKrx32fx3Edq4dBjKd95NlVUcj/hO3XquwwIDAQAB
AoGAYkqzFPu7GczyfRycgMJ1gAZHbXVqKMT2F1+/LthNYKc0rTP+MScnr/UeOmTv
YLkh4W9avfLtvFgxd7r2hc0gdrlMKd8lQ3plZpLqHNBKkKVYgPyJg8qZBC8I2YWq
Y6+4qjC1GN18gF8g1AhQcRjRtKqpiqVp1VjxdK+xPiYPEKECQQDzuhjCcL8zHDT6
H6YryaQK609uxWuzPFesddkRvKZ3cgmxx0ZUh7E2ukBo9CmdCUocs1doMN+Ta96v
9d7n0UWJAkEA1LRXFXbTlNeFwPVhd8M3FzHU1j5S1agM2U8CfbkzhFDH3qz6Ia+2
+Hk75AwrlMLmnuABtWTAig6aPP6C5MSK6wJAVIcBGUZS+V3Z/blGPz9ydhr/9HHh
lUrjOTux6dXcgeZ5+D8dZCmfS1SzC/NKD11uZ5/HO6pfj9hEZhBGm21XyQJAb3Pf
fZu52e/kYesxmzNrFnhB8dDOTq2zrdo8j+wPFnHNiNxSZHxR/3hm7WODInvNo8n0
mzujt7NXFka2B3EE6QJBALRfEPQB4HeRhECHON4htHLBJBO6lo3jWN0myW0msuPu
M5Q9Y4zwvEcrduc4v2FPfVcaCAoM7NcHwPJCtfyO7ok=
-----END RSA PRIVATE KEY-----
Kaspersky license keys:
053A10DD.key
kaspersky-053A10DD.key.base64
S0xzdycADQpTZXJpYWwgTnVtYmVyOiAwQzdBLTAwMDRFMC0wNTNBMTBERA0KS0xzdwAAra0BAAAA
/AMAAAMBAAgBAQAACQcBAAgBAQAACQUVAAEoCQBFbGl0ZWNvcmUBAAAJAxYAAQEBAAAJBQEAASgN
AGZvciBFbGl0ZWNvcmUBAAAJAQMAASgFAEluZGlhAQAACf8BAQABKBYAS2FzcGVyc2t5IGxhYiBr
ZXkgZmlsZQEAAAkBBAABC90HAgAAAAoAAQAACQErAAEJAQAAAAEAAAkDGgABCQAAAAABAAAJBQQA
AQlQwwAAAQAACQEBAAEJAQAAAAEAAAn/AQcAAQlQwwAAAQAACQEIAAEoIwBMaWNlbmNlTnVtYmVy
OiAwQzdBLTA5MDIxMS0xMTAyMjIuIAEAAAkBGQABCQEAAAABAAAJAQMAAQltAQAAAQAACQEOAAEJ
4AQAAAEAAAkBDQABKEYAS2FzcGVyc2t5IEFudGktVmlydXMgZm9yIEVsaXRlY29yZSAoU2VydmVy
LCBuZXcgbGljZW5zZSBzY2hlbWUpIDEgeWVhcgEAAAkBFwABKCQAOUQ3NkJBNEYtQjYwRC00NzQ4
LThCMjgtQzVGMUIyMUMxNjc5AQAACQEKAAFJAwABAHoMAADgBAAA3RA6BQEAAAkBCQABKBoARElT
VFJJQlVUT1I6IEVsaXRlY29yZQ0KDQoBAAAJAQIAAQkEAAAAAQAACQEdAAEJBQAAAAEAAAkBIwAB
KBIAMEM3QS0wOTAyMTEtMTEwMjIyAQAACQEfAAEJQgUAAAEAAAkBIAABKAkARWxpdGVjb3JlAQAA
CQElAAEoCwBLTDY1MjlOU0JGUwEAAAkBGwABCZADAAABAAAJAQ8AAQvZBwIAAwALAAEAAAkBJAAB
KAAAAQAACf8BUQAICR4AAAABAAAJAVIACAkeAAAAAQAACf8PnxJXDQo7OjEwNFNOUmFaTXVmVTIx
K1dBUUw5Q1FwT3NMVlV4UEFQZkNEL1NZd2Ztckt4T1NLT0szSU0yQ3RuZEZpTms3ZHo1SmRsMnlZ
cHFESE9iSWZXb2xkNmtrSnYlJQ0KOyAwWExTem5wZEk3MWZCMzAwZTdVd2oxUFVkUWZOcDlZOTRI
UmxsbGt4SW9qVUFHdUhVTUYvaFY4UnRqra0=
0316D86E.key
kaspersky-0316D86E.key.base64
S0xzdycADQpTZXJpYWwgTnVtYmVyOiAwN0JDLTAwMDRFMC0wMzE2RDg2RQ0KS0xzdwAAra0BAAAA
/AMAAAMBAAgBAQAACQcBAAgBAQAACQUVAAEoCQBFbGl0ZWNvcmUBAAAJAxYAAQEBAAAJBQEAASgJ
AEVsaXRlY29yZQEAAAkBAwABKAUASW5kaWEBAAAJ/wEBAAEoFgBLYXNwZXJza3kgbGFiIGtleSBm
aWxlAQAACQEEAAEL2gcCAAAAFQABAAAJAxoAAQkAAAAAAQAACQUEAAEJUMMAAAEAAAkBAQABCQEA
AAABAAAJ/wEHAAEJUMMAAAEAAAkBCAABKCMATGljZW5jZU51bWJlcjogMDdCQy0wODAyMjAtMTUw
NzA0LiABAAAJARkAAQkBAAAAAQAACQEDAAEJbQEAAAEAAAkBDgABCeAEAAABAAAJAQ0AAShGAEth
c3BlcnNreSBBbnRpLVZpcnVzIGZvciBFbGl0ZWNvcmUgKFNlcnZlciwgbmV3IGxpY2Vuc2Ugc2No
ZW1lKSAxIHllYXIBAAAJARcAASgkADdERjA1NThCLTlGOTAtNDE0Ny1CNDEyLTQ5QUZDRTE3NDQ3
MgEAAAkBCgABSQMAAQC8BwAA4AQAAG7YFgMBAAAJAQkAASgaAERJU1RSSUJVVE9SOiBFbGl0ZWNv
cmUNCg0KAQAACQECAAEJBAAAAAEAAAkBHQABCQUAAAABAAAJAR8AAQlCBQAAAQAACQEgAAEoCQBF
bGl0ZWNvcmUBAAAJARsAAQmQAwAAAQAACQEPAAEL2AcCAAMAFAABAAAJ/wFRAAgJHgAAAAEAAAkB
UgAICR4AAAABAAAJ/7x3tQwNCjs6MTBxOWZtbStCWXRwN0NzNVV1dU5Ea2ppaTNPaERraWpLVlFa
VDFrRTN2RnR5ZG9aTG5iUk5LRE9KdUhXbjlEZkQ3Wkd0VEZKTjNZZFpMQ0hqM0JiZlpqZiUlDQo7
IDBYTFN6bnBkSTcxZkIzMDBlN1V3ajFTNTlhcUVTeW9wWnZkeHg3czNKT29zYUJrSWJQNXg1czBq
aHitrQ==
SSH host keys. SSH is run on TCP port 222:
ssh-hostkey.pub
2048 35 23178304127391053134639083855042652968257017487248714289440944074345544197073367934275067382138342595922854198773473362149187429589211588690241225077935146243500409620985015706704134157338119525281498899096023145572448050960142245589480162309456185807776043089290451042235810319339234735452828481874956059229217315046402077465958412694739848655959942060360292721914185566944685578412514086483450261861706864655780403651890928799805363542268510358235314703532093327713100614934847080258051943853502840222131140959127457801042953627742113484869153125370094179859128942490254330920318324474144901652212339292637649329539
2048 a5:25:56:0f:2b:e4:a3:90:46:ca:42:91:24:77:e4:10 (RSA1)
OpenSSH RSA1 private key, version 1.1
ssh-hostkey.b64
VlRGT1NVbEdRbE5UVmxwQ1ZrVlZaMU13VmxwSlJWcEtWRVZWWjFKck9WTlVWVVpWU1VSRmRVMVJi
MEZCUVVGQlFVRkJRVUZCWjBGRApRVU16YlRSa04wMTJTMlpxUVhkbVJVNDFjZ3B3V0V4RFVua3hT
bkJVWWt3dlIzVmhlRzkxV1dKbFJIaEdlbFV2YVZGT1JsaEhUVE5RCk5XVnFkRkpSVVZGQ2RqSXJR
UzlGT1hSeFYwVnVNMEZQYTBReGNHeGhZbVZoZDBRd2F5OVNDbWQ0VVZkYVpsRldOMHNyUmtadWNW
WlEKUVhWRGNuWldRazV2TUhkUUx6ZElaMFJEYmxkTVMwdHRjQ3RVWjBoclptVTJjMGR2T1dkNmRI
VnBMMkYzYVcxd2RqTk9WWEF3Y1RCSgpZbEVLZFdwWmVrOTRTbE5wVkdGNlVGUXpTalE1VDJwR1lX
UklLMkpwVlVaMGFrcGpXbE15UWxsRFNGRkthMm96ZVRSd1ZEZExVRk0zClpWWnFSSFJ4YjFwelUx
SlVTM1E0WWxScVJGRXZid28wT0RWSlRsTlVWVTFqTnpCeFMxSndORUYzT1ZBM1UwbFhjVFZJU1dO
bllrdHYKWkV0MmMyZFdUVXBVYkcxT2RHYzRjbEJNTURVNFFrNVpiSEJPTnk5aE9UZHNkekJET1VN
dlZuRXpDalJzVlM5bVNITnhkbWxyT1dkdQpSalZVYkRKRVFVRlpha0ZCUVVGQlJHRnlUbkZ6U0M5
U09UVjJNMUV3Ym5BNFEwVk1WR1ZWWjFCVVQwUTJVRElyUXpsUVNtWXZXWFZrClZsQkpRMGdLTTFk
emIycE5hMUZNU0VwTFYybGhObU5qVWtzM1dEaG5OM1J1YUZsamJpdGljREZwVVZoR2NFVnVUa0pH
YVd4SlJIUjMKVm1KTlZGVndSblZqWTNaNGVIUTNRbkZSVDFwcFJVcHZVQXBZVkRWb1NEUlRaRkZh
Tmt4QlVXRXJkalJXTld3M1RHa3dkVGt3VTFSUwpWMjFvWkN0alVYSm1TbWN6ZDNaamRIUlFORTkx
ZFVGaFIwTkNSRGRsTUdaeU1sTjFXR3RxTkZaR1YwRllDa3h6VWxVNFlYQk9kMGdyCmNrSlhTWFJo
Y1VKcU1EbDJZMUkzZGtkSVVqUTJMek40VlVkeE5WVk1TM1ZyYzBsQmVYWnFkWGxzTldOV1JFRkZj
VzFNYjNCM2RrNVUKTnpGa1EwVnZhM0lLTmtsalNHOXJRbUZ5TldnM1JrWTFjMU5hWldkME0xVlJi
azVJYWxkdFZrWk1SRU5ZYURjNFpqZFlVMngwUWpCRwpPRVJsV2tnd2FVeEphMk4yVFhnNVlraGFR
MjFMWlZGRFVrUnpSQW92VW1wNFZXMWxVaTlzWlZCb2N5OTRNRlp5U1ZsM1pqQXpUVVJVClYxUmxV
RFZyY205VlJ6Y3JSamhMWkRobWQyRkVaSFpNYTBwdE4wRXlkRFpSZUM5R1p6RkthMlZSVlhaaWNF
ZGFDa05ZVmxCV1JGUk0KTm1oeFVrVXdlVmx2VlZwYVEzVXZUVFpvZERrellpdG5VVUY2UVdnM1lu
ZHFWbGRLVVZkUFVpOTFSVWd2YW5KTldqWk5TazVQUkVWbQpjMGR3TVZGeWVHRkNaRzhLVUV0UmVV
MU5abXB4VG5kQ1VVOXNPRWQ0ZVdKQ1FVUlRUa0V3UTB4c1RVcEdWRW9yWWpaQmNXMUtlbWwwCk0y
eEtVM1Z0UkhCMFVFcFBWVnAwUkVSTFFrOU1VbUZ0Vm05Rk5uVlZRUXB1Ym5KUFRtSnhlVU5ET1ha
elZtVlVlV2x0WVhSamJVaEsKZEZOVFVUUTNhVEpTY0dKNFoyWkNSM1Z3ZEVaRVZuTkdZMVZqUXpW
d05qQllOakZSV1M5NFREQXhjemRuTkRKb1NUUm5DbkJQY25SUApjMUZQTmpabFVteEtlVXB2Y1ho
amRYaDJhamszVkVWb2RpdG5ORzUwZFdkVVJqVmFVVkZCTXpWM1pIZFJRM0oxYzNCeU5tdFdlbFoz
ClUyTk5PRWh0VVhWbE9VaFBVMDRLWjFkeE1rcFlOR1JIVjJsc01qaHBZM0p1VVU5cU1IZzRTblZo
YldwNVJGWkZjblI1U1V4NWJrRlAKZURBeGJTOXZSalpuUlhCYVFXdHhaRWRDYVdGNlZrcGlXRTlF
TjI0eVZtMTBjd3AzUmtwNlJVUlNNMGxFV1ZaTlVDOW5OMlpwU0ZWbApkVUpYWVdwclNGSjNNRTQ1
TWxKQllrWlVlRFJDUm1aeGFVcDBlR1ZCVnl0VFZFUndkR3hCVFdOQlFVRkJRUW89Cg==
Miscellaneous keys:
root_pubkey.pem
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAzMC1VjIT81SDM7O4zoVe
NlRdujsoBlfFI9h4kP6Cx4Ih6IkZwX+wHcJ2pBrZpKMxzwHXwoz8rOR/bQCcWhVo
b9+0xzVkfhpije1nkbx63iEn+mYTEUZBKLxq1I7FuuNVfS3EswcZyPrT++C3y/2M
7iujoeDqs/7dI+oCtdc8oYeaeN4Sady89E3vUASjKN3bBTkWgknG3TEXOfqp6/W2
9DupR9vtk1D6SDOnsveRc352L5d9ojbtIYU+K2GgJZ6hpdShH8XyZKJCbEN9iFHF
dDjVEj2u7wBcAgSA2BZrlsdW5ZJLGLYc91kU4MqCtdRhG+4WS7l2XsgKdCI4JmKT
FwIDAQAB
-----END PUBLIC KEY-----
Administrative user is set and reset through SQL:
INSERT INTO tbluser (userid,name,username,password,dob,createdby,createdate,renewby,renewdate,active,emailid,securitylevel,groupid,securitypolicyid,accesspolicyid,ipallocation,allottedminutes,totalusedminutes,expiredate,authserverid,bwpolicyid,printingpolicyid,zoneid) VALUES (NULL,'cyberoam','cyberoam','cyber','2002-10-01','elite','2002-10-01','elite','2002-10-21','y','elite@elitecore.com',1,1,0,0,6,0,512,NULL,-15,0,0,0);
select @userid:=userid from tbluser where username='cyberoam';
INSERT INTO tbluseraccounting (userid,usedminutes,uploaddata,downloaddata) VALUES (@userid,0,0,0);
upgradekey:
090600078.2
Update key extraction and
Update key extraction and usage:
I glanced at the site on
I glanced at the site on removing the certs, but I didn't see any in Torbrowser (Firefox ESR 10.0.5) in the section it was pointing to.
Edit=>Preferences=>Advanced=>Encryption=>View Certs=>Authorities
Instead, I see DigiNotar references in:
Edit=>Preferences=>Advanced=>Encryption=>View Certs=>SERVERS
These references were not mentioned on the site you posted on removing these entires from the 'Authorities' area, there was no mention on the site about these existing in the 'Servers' area and what we should do about those entries. There are two entries in the E/P/A/E/VC/Servers section:
DigiNotar (which expands to reveal 4 entries)
DigiNotar B.V. (which expands to reveal 2 entries)
What should be done with these entries?
I'm working for a Cyberoam's
I'm working for a Cyberoam's distributor.
Cyberoam is a UTM solution, not focused only on DPI. Actually, this is not really a DPI solution at all.
One of the Cyberoam features is the HTTPS Scanning for Antivrus. When you enable it, the Cyberoam unit will dynamically generate a certificate for all HTTPS websites so the user browser will communicate in HTTPS with the Cyberoam, and then the Cyberoam will do the "real" HTTPS traffic with the website. It acts like a Proxy. The purpose is to be able to scan HTTPS website with Antivirus.
You need to understand that Cyberoam's appliance are installed in corporate network as a gateway firewall. So the corporate choose if they want to apply the HTTPS Scanning on the unit. And if they do, they know what is the mechanism of it.
I fear you have raised a non-existing vulnerability.
I have escalated your article to Cyberoam's management team, they will surely answer you soon.
There are two issues here;
There are two issues here; one is that a Cyberoam certificate is being used to intercept all traffic to torproject.org, another is that all Cyberoam devices share the same CA certificate and hence the same private key.
How can you be sure that the device being used in this case is not doing DPI, but "just" HTTPS scanning for antivirus? And how come the device is only intercepting traffic for some sites - and not all? Is there a way to specify which sites you want the device to intercept traffic for?
Hi runa, Thanks for drawing
Hi runa,
Thanks for drawing my attention to the vulnerability of Cyberoam. I use a sonicwall appliance in my office at india. I would also like to report the same thing on my sonicwall appliance. I went to my sonicwall appliance to download the CA certificate as mentioned by you in the blog post. I was able to download the certificate from my appliance. Screen is shown below
http://www.picvalley.net/v.php?p=u/2055/11258394806391790141341517411UM…
Finally I also learnt that sonicwall have a website where they host the appliances for live demo, I would share the links below
All the sonicwall appliances are available for a demo from livedemo.sonicwall.com
http://www.picvalley.net/v.php?p=u/1690/14420756404065594191341517413ge…
NSA – 8500 - https://realtime.demo.sonicwall.com/main.html
NSA E5500 - https://nsa.demo.sonicwall.com/main.html
NSA 2400 - http://2400.demo.sonicwall.com/main.html
NSA 250 - http://nsa250mw.demo.sonicwall.com/main.html
NSA 220 - http://nsa220w.demo.sonicwall.com/main.html
I downloaded the certificates from all the above said appliances, and they appear to have the same details… and the same private keys…
The screen below will show you that I have downloaded each of the certificates from a different website
http://www.picvalley.net/v.php?p=u/2864/84257012810543838161341517419Wj…
I aligned both the certificates together and saw there is no change in any certificate… both appear to be the same. I wanted to know if the sonicwall also has the same vulnerability like the one you have listed on your blog post.
http://www.picvalley.net/v.php?p=u/2967/16816463827450592701341517436pU…
I have also recorded a video of the same but unable to post it here, here are the links of the sonicwall certificates
http://nsa250mw.demo.sonicwall.com/SonicWall_DPI-SSL_CA.cer
http://2400.demo.sonicwall.com/SonicWall_DPI-SSL_CA.cer
http://nsa220w.demo.sonicwall.com/SonicWall_DPI-SSL_CA.cer
https://nsa.demo.sonicwall.com/SonicWall_DPI-SSL_CA.cer
http://www.sonicwall.com/downloads/SonicOS_Enhanced_5.6_DPI-SSL_Feature…
ALSO OUT OF MY CURIOSITY, I WENT SEARCHING FOR OTHER VENDORS AND FOUND THE SAME ISSUE MAY BE WITH FORTIGATE DEVICES.
Fortigate Certificate:
http://kb.fortinet.com/kb/viewContent.do?externalId=FD32404
Runa, after reading the TOR blog, I am very much concerned about the security of my organization. We normally do transactions over the internet all the day. I would like you to revert back to me on the same. I am not in a condition to remove the device.
Request you to kindly reply ASAP. In the race of UTM, please suggest who is the BEST vendor…
I will have a look at this
I will have a look at this in the morning. Can you please email runa@torproject.org in the meantime?
Runa, after reading the TOR
Runa, after reading the TOR blog, I am very much concerned about the security of my organization. We normally do transactions over the internet all the day. I would like you to revert back to me on the same. I am not in a condition to remove the device.
Request you to kindly reply ASAP. In the race of UTM, please suggest who is the BEST vendor… SEO Company USA
Runa, I believe it's the
Runa,
I believe it's the individual's choice how to be protected. If you want your self to be protected against encrypted threats, you must allow security device like Cyberoam to intercept your traffic. It can be any XYZ traffic including traffic like of your TOR application. Finally, for a network admin like me, getting protected and not allowing any one to bypass Internet security using application like TOR is more important.
It's like doctor and patient relation!!!! If you do not allow doctor to treat you, you can not be cured.
I said by other blogger, Sonicwall also use the same method, so whats wrong in this??
The Jordan user seems to be
The Jordan user seems to be a private user (Twitter, Gmail, Facebook usage).
He was surprised when he received the fake certificate and did not know about the Cyberoam device interception.
You describe a different situation where a company monitors employees PC usage (presumably after having them notified about his rule).
Your justification does not apply to this case. Likely the interception is done by the Jordan user's ISP or upstream provider without user's knowledge.
In addition your explanation about the undiscriminating behaviour of the device does not appear to be correct. As the Jordan user said the Gmail connection, which is also an encrypted https connection, was not intercepted.
Runa, I believe it's the
Runa,
I believe it's the individual's choice how to be protected. If you want your self to be protected against encrypted threats, you must allow security device like Cyberoam to intercept your traffic. It can be any XYZ traffic including traffic like of your TOR application. Finally, for a network admin like me, getting protected and not allowing any one to bypass Internet security using application like TOR is more important.
It's like doctor and patient relation!!!! If you do not allow doctor to treat you, you can not be cured.
I said by other blogger, Sonicwall also use the same method, so whats wrong in this??
Hi, You should read this
Hi,
You should read this answer article : http://blog.cyberoam.com/2012/07/ssl-bridging-cyberoam-approach/
All UTM appliance : SonicWALL, Fortinet, Watchguard, etc... use the same approach as it is the only existing one !
I don't see any vulnerability there. Yes Cyberoam is using a man-in-the-middle approach to scan HTTPS traffic, but it is not hidden to his customers. Customers have the choice to activate or not this feature. If they don't trust in Cyberoam, they just don't activate the feature. This feature is not activated by default.
Lawful interception in
Lawful interception in business is not done by forging certificates.
Employess' browser are set to use a local proxy and have the local
proxy certificate pre-installed. The local proxy fetches all https
requests, scans them and pass them on to employee.
As Eclipse Micro Computer is an U.S. company holding
Elitecore/Cyberoam, the Torproject should think about talking to
a lawyer.
Cyberoam interfered with protected communications, forged
certificates with Tor's name on it and with this damaged the
reputation of the Tor project.
Cyberoam cannot excuse themself by saying their device has
been abused, because they admitted in their own blog that this is
their standard procedure.
A favorable judgement should be worth 10 years+ of funding ;)
Today I come under massive
Today I come under massive spam attack. I have told all goverments in world about this attack but they are doing nothing. This is not good for me and I want everyone on the internet to remove moreacting@libero.it
Already I email 4chan.org secure server, ripe, interweb, cloudflare and all governments but no one remove my email from internet. Justice must be brought to my account and the people told!
The world must know not to send emails to me any longer! The authorities must act!
And to reply to you, the TOR
And to reply to you, the TOR user who has raised this "vulnerability" has seen this fake certificate only for torproject.org because this website is categorized as "URLTranslationSites" which is a default denied category. So, when the user tried to reach your website, the Cyberoam has blocked it and to be able to show him a Denied Message, it has used this fake certificate.
I don't think so. Otherwise
I don't think so. Otherwise the user from Jordan would not have
been left with impression that something is fishy if he had seen
a message like:
"Torproject.org is blocked by the Cyberoam DPI device because it is our category of evil hacktools."
Faking a certificate for Torproject.org would make sense if one
wants to interfere with the download of the Tor software and
swap it with an altered version.
If the the user also happens to download the GPG signature
the previous download would just be seen as "broken".
"There are two issues here;
"There are two issues here; one is that a Cyberoam certificate is being used to intercept all traffic to torproject.org,"
Not all traffic to the domain, only all traffic to the domain from the user who is behind a Cyberoam device. Some are asserting, without evidence, that the Cyberoam device is in place at the user's ISP, when it could be at the user's *employer*.
"another is that all Cyberoam devices share the same CA certificate and hence the same private key."
Which is the case with most UTM vendors in the default configuration. Best practice is to put a corporate subordinate CA certificate in place for this purpose, and push that out as a trusted certificate to all corporate endpoints to avoid the warning messages. It would not be a good practice to push out the vendor default certificate to all corporate endpoints.
.....
.....
What would GCHQ or NSA do to
What would GCHQ or NSA do to achieve something similar en-mass, especially as House of Commons is discussing Communications Data Bill which would permit it? I realize that they're wholly able to do it as NSA utilizes Narus STA 6400 amongst other devices, but would it also require CAs to be compliant? Or rather complicit?
hello there. This is
hello there. This is probably not related but I'll put it here anyway.
I normally check the Tor blog on a somewhat regular basis. I am now using the duck duck go HTML search engine from within TAILS and I noticed something weird. The Tor project page that came in the first place in the search results was http://www.torproject.us/
not https://www.torproject.org/
I found this weird because I'm used to seeing your page through https and it was in http.
I am using this ip: 93.182.129.84 which according to IP check is from Skane Lan, Lund.
My question is... Was I just victim of a man in the middle attack? I mean I went to tails page from there and https came back... but then clicked on the tor browser bundle instead... and it went to http://www.torproject.us/download/download-easy.html.en
I am not very technically able... but is it just me? or is this very fishy?!
No it isn't, nor is it a
No it isn't, nor is it a concern. It's a mirror which permits access to visit The Tor Project as its URL could be restricted dependent upon which environment access is being attempted from. It's genuine, it merely duplicates whatever content is available via The Tor Project every so often, but it isn't associated with or to The Tor Project itself.
That makes sense. Thanks for
That makes sense. Thanks for the clarification :)
Very interested what the
Very interested what the outcome of this will be, we received an email from one of their sales managers that insisted on having a meeting to discuss their products, I neglected his email, then he started spamming our company over the phone after a couple of weeks he gave up, but I never had such an aggresive sales (quotes: 'I must speak to x urgently', I insist on having a meeting, blah blah blah) Taking the above into consideration (And I wasn't quite impressed with their portfolio, has a high copy/paste ratio when looking at other vendors) I have a very strange feeling about this company and with all do respect, have more confidence in the Torproject then yet another 'security' vendor that communcates with Skype/MSN, has something going on in the US but whatever number which they use for phone is +91 country prefix.
Clouds… clouds… clouds
hi all privacy fans. i know
hi all privacy fans. i know this is off topic but can someone recommend a privacy oriented VOIP software. Like an open-source version of skype. with end to end encryption or something. It doesn't have to be able to make calls to land line phones, just between users, like you do with yahoo,msn,skype.
does it exist?
No reply, reposted for
No reply, reposted for answers:
I glanced at the site on removing the certs, but I didn't see any in Torbrowser (Firefox ESR 10.0.5) in the section it was pointing to.
Edit=>Preferences=>Advanced=>Encryption=>View Certs=>Authorities
Instead, I see DigiNotar references in:
Edit=>Preferences=>Advanced=>Encryption=>View Certs=>SERVERS
There was no mention on the site about these existing in the 'Servers' area and what we should do about those entries. There are two entries in the E/P/A/E/VC/Servers section:
DigiNotar (which expands to reveal 4 entries)
DigiNotar B.V. (which expands to reveal 2 entries)
What should be done with these entries?
Cyberoam devices all have
Cyberoam devices all have /_conf/csc/cfsconf/proxy/skein/skein.conf with:
Cyberoam_SSL_CA.pem was available on the Cyberoam website for a while, but is gone now. The contents of Cyberoam_SSL_CA.key is:
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,32F7DF8807E09313
tAg/PFbnt1RMq2EIpDl7ZBq4vLaaYm6ne0ITnwd09+6yHZIrnoEEI4dVnGsCVkdk
dD5XGmJIQv7h0UF9QV3yOysa8hzJEvZtAwRyF0Qx9RL6rwRyL4Udim5ZP7m6h9/B
q9rK5rG0zVPGeTuTHEI58etNaR4v0uWoNpQ/jLuEdrnYnh83CuXszQZ85qqdeOqO
ZihH0alUsDlb5Yq/ejdLbc9PWnov/I7ERjA6weBbif5uJBp7VkDA7GVbmboAP+wo
kM9+W/xtppIcMKeFAqRPIqXOqPosnmJcZbIKnGErx8XSIjU3wOWnRpDz0mbpLW6j
KJS2t0VLXWv1klqS5dMjLRyp0UUoIe7RwHeDqLZ1gQaeUkPOMVflkyB2+j4HISrU
JQtdZe2HdYtBCsKGFjL7z5WSZFbaK3/FpTXaiAgyZZ375s6sRyD57VIYg2dl9Vd+
3CR+QHpsQ056Pm21cScLFjatcI+9j1750BAnW7qP0ki54WAStH11bw2LFKaKAiEG
SvkuGhoMZZIqMRSGHkVW4pLzIlvmwiissKxclBLt/dk4gju4ZQAvS1vo/i9qNHNb
RWkGhtUAUlqYITWWh3sKiYHMFuBE6Tncw91DZ1nLAIVfF36lBY55UVKUzxVf40IJ
URnlUZIC+IlZEuaRsd+ro7Lv6HMqDSp+pxaSXUJ0hPi19iA45hUNFoE0EIU4onfj
SWFQbiiLtJPCr1hbNacjOlzIh2MMUgVp4tBVpBdC+1s/HA4pbugZaPWTP0UGSI3K
H3KJpwYhZqxuNYVPDBpNR3pH1jP5q0zSTYw8VIUVcQI77YEpwWObGL39+Bdudy/S
qJKbAYSqoLmcK4jlQcd13ixzcXVg4rIgkH8NNdUoLz33LjHDBHR5toOcSesT/AQy
uJrRR0DfiNEtan0QdlDvMV2yKFwUAQC0opS26KfuMR55AbfxZ+AJGzRmMwZ4tJfG
GmwVQ8th7XLPiQvZSWh4cddoVGuItaX9mcnbLygtZIi4pLKdeKUNV7qYLzPkWNK7
hMx2QEzxlv3Q4fTI/i7wgRIpv7LwzwKNTTL2LHNg1q7Akzc/LQWk/02WIL7Q3/y3
4YFjHiP1OHDkyZJNinSkwxFntqdXSuqjmwSPN0FmXIbNN4TyRRGi8CFMsX9qxv59
WkAki2K1UCLv6Jy0y/bPpD/7hGt+IAviQbxvWYvt2s+YmSLNPXEV79ssarvFOf7L
6cIBYcabhYYAGpJtIQAmrMNrKljnS8nr71tn4xBaYTzbNWmvQMJboeFpiWKwr09N
FQI6EephiK34TqF3ozvaXKQtGaxcaF8EYP2tSevpRE0IcpiKaaAW6YEnDTAmRYVy
PIH7HO5ObbXyIGVOe5hPfFBPpMfFWzno2U9rqEW7G9d4xBnlurCYO3G8bCQj0Odt
b53kCcSdl7Kqj7eNDOq21NiWDt4a5Y11Ql/n9c7QDxCodqQGGzYMcHQRTP4H2ePf
vItU43sDNWpRVUULr2Q9Zjw3MniR0v9mnd/y6kG7lOTu1kxd1gt+cAf2HhBwNJri
2IKD+dVHmFvkNekFoagFDKiDvNmKR/+O1aPZWNBc2Zf7j68vvJ41JNduZrnJvXBv
-----END RSA PRIVATE KEY-----
lulz thx for this leak
lulz thx for this leak
Are you sure that's the
Are you sure that's the correct key formatting? Perhaps the blog formatting has messed it up?
It's an encrypted private
It's an encrypted private key. You'll need the passphrase. See
rsa(1).Here is the decrypted
Here is the decrypted key:
Runa, from SonicWALL
Runa,
from SonicWALL perspective and from all vendors that make ssl-dpi inspection, it's obvious that the way to manage that check is a man-in-the-middle activity.
BUT ... the sonicwall permit you to choose what certificate to use and it's obvious that ssl security is based on user check of the certificates.
the sonicwall have the capability to check for viruses, malware in general, ips/ids and applications inside the ssl IF needed.
like the KNIFE on a table ... you can use it to eat or to kill or to save a life .... we produce good and well documented "knife" ... just that
N0F3@r
-----BEGIN RSA PRIVATE
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEA4ax+WmILhtQDBuW1VAY3gAKoOBGLD34GyKXHBKepRDLgn7n/
3sYuXj4D8Og9sjhdBuw+o+jji2IFtZVbMjas6NU2BIX8dynmtmTn//d6ACALXEmD
6JVP2Wqw+/ZxCQaf+JmPz9zX/6r2y8VpB1b9w1pEjQTUmAh9yexeWiGX+d0/XvkO
+pAFCB8pYUYmU0AiXsU2XqZMj09rMw6tgaQkrQPP2N/op8qwT+4U35UaexCxjnta
SqnoT3ulsTB+adlWcI2VP/+Lg43sW+TIe9EVu09ZW4BBQ2OjlqSHeVtWfeVwZySr
gtyQU7FvDKJeMnGNc/vDlax1+9/zXU7wyyPd5QIDAQABAoIBAQC/mArOAV934JeR
S4RfCcgkzhyzPXGqfXyU7OnCcfWrCObbtLYfFHJZYJ1H8mQu4ttX/UpRLm/A7j+a
omsCfpjeM+XggUCOiuxs/c5Z6mmRoaMDfwaWd+2K0KHhyKC+4Pj/vp/yAbUAQs20
wq0gpiJbsE9yyh8T1GG3BQ41xz+XyT63QnzO3cKzYa1DQgDmOm3IGU2dd94dLora
Vqds7/+uMly5uk9837Wdfi28jH4xxl9/3MmIdVmsF8cx2wbyRn//4rV7H/YnW/2B
03lKtH4QYes1Xguxt4pSYbnSm9+cyoRC1vlk5G3v3TJVpKf4T1ZBGNvniL1clzTB
MD8BTQoBAoGBAPa5ZlCsx4JatTkb6s5YBTVDem3CLVz86pZZUmSGCPmRx47Kz9M3
/tjDSebwgZLA/5EWSaJ5bbYYlSUttzkEScDITRUK6l8csK1Hg2sB/OM9UE1hrUgr
jL0jaB8XiEEmphuEKvmp9keSYHzt4fnUr6Xa31+JpkOKOitf0Oe2PpmxAoGBAOoo
fnGEGaDRZFc8tdXmkMfrOZrT4U6WRiuQ9YN0TWiVigQeaPg3AVAI9iLXlR5j4NQs
rmFnmeZPQrpU3U/J/ChrGfAmjifXOrdqSSr7zu4eAD6zXiOuXpfIUUuddtUIudxa
N/RXdKUMy4sU0WiKHUTUtQwvMPt3CY/IUYidSaB1AoGBAPMwb89ZXxX3/uUZxWo6
jHeh2Y1SdpBPo5Mq2/HFxBbrQH5ZHlydtw9F/xQpQC69GauTAmWptyBkPq50z0Le
HSxuwrvZFIdHqkZCVSEmxnPePcboXnriokjUG496DI3bYKOCtTF9/Ak0GPNLLxCo
ObILeV2cOkwcdZXHTgz3L+EhAoGAXLpWgFugzoe9ZbKcC633zcPAFykrAzUNarlI
EJug//agJktopEscEPbLija3TcadxUhAckBVuNfQg/uRfMRvQA5RwkFycCKSlQnZ
GdWIN9HXpPzhHd4yhYcFcp1T7r864yEzIWb0wVvUyyoeV3jCaHyXidCyZBLazX61
kxU+j/UCgYAQUUcebPBkQlOnnWIxBuRTc6uLBs6QLiJs4TvIKmk0WNLZEMiBdkHG
d4kzMmHRbz8XjtLEMRRfsZKEdn9FpjR+rc02QBU6BzdDpUj6gTJwaXeEeRrzq+Cp
QbV64/ky3NauHItm2pxZZJLUTqjcC7mjoCEpJhyh3OaFVzxidJZM1A==
-----END RSA PRIVATE KEY-----
We need an official Tor
We need an official Tor discussion forum.
I didn't see this issue mentioned in Roger's *latest* notes post, so for now, mature adults should visit and post at one or both of these unofficial tor discussion forums, these tinyurl's will take you to:
** HackBB:
http://www.tinyurl.com/hackbbonion
** Onion Forum 2.0
http://www.tinyurl.com/onionforum2
Each tinyurl link will take you to a hidden service discussion forum. Tor is required to visit these links, even though they appear to be on the open web, they will lead you to .onion sites.
I know the Tor developers can do better, but how many years are we to wait?
Caution: some topics may be disturbing. You should be eighteen years or older. I recommend you disable images in your browser when viewing these two forums[1] and only enabling them if you are posting a message, but still be careful! Disable javascript and cookies, too.
If you prefer to visit the hidden services directly, bypassing the tinyurl service:
HackBB: (directly)
http://clsvtzwzdgzkjda7.onion/
Onion Forum 2.0: (directly)
http://65bgvta7yos3sce5.onion/
The tinyurl links are provided as a simple means of memorizing the hidden services via a link shortening service (tinyurl.com).
[1]: Because any content can be posted! Think 4chan, for example. onionforum2 doesn't appear to be heavily moderated so be aware and take precautions.
Here is the decrypted
Here is the decrypted key:
The site you link to for
The site you link to for instructions on removing certificates doesn't have correct instructions for IE and Chrome. Deleting certs is not the complete approach, putting them in the Untrusted certificates store is the right way to go on more recent versions of Windows.
The site you link to for
The site you link to for instructions on removing certificates doesn't have correct instructions for IE and Chrome. Deleting certs is not the complete approach, putting them in the Untrusted certificates store is the right way to go on more recent versions of Windows.
WAKE UP!! RE-REPOSTED No
WAKE UP!!
RE-REPOSTED
No reply, reposted for answers:
I glanced at the site on removing the certs, but I didn't see any in Torbrowser (Firefox ESR 10.0.5) in the section it was pointing to.
Edit=>Preferences=>Advanced=>Encryption=>View Certs=>Authorities
Instead, I see DigiNotar references in:
Edit=>Preferences=>Advanced=>Encryption=>View Certs=>SERVERS
There was no mention on the site about these existing in the 'Servers' area and what we should do about those entries. There are two entries in the E/P/A/E/VC/Servers section:
DigiNotar (which expands to reveal 4 entries)
DigiNotar B.V. (which expands to reveal 2 entries)
What should be done with these entries?
https://blog.torproject.org/b
https://blog.torproject.org/blog/diginotar-debacle-and-what-you-should-…
It isn't associated to the
It isn't associated to the subjects being discussed and is wholly unrelated as those CA public key certificates were revoked by its issuer, therefore any public key certificates authorized and issued by said CA are distrusted by Web browsers. It isn't necessary to do anything.
R.I.P
R.I.P
Private-Key: (2048
Private-Key: (2048 bit)
modulus:
00:e1:ac:7e:5a:62:0b:86:d4:03:06:e5:b5:54:06:
37:80:02:a8:38:11:8b:0f:7e:06:c8:a5:c7:04:a7:
a9:44:32:e0:9f:b9:ff:de:c6:2e:5e:3e:03:f0:e8:
3d:b2:38:5d:06:ec:3e:a3:e8:e3:8b:62:05:b5:95:
5b:32:36:ac:e8:d5:36:04:85:fc:77:29:e6:b6:64:
e7:ff:f7:7a:00:20:0b:5c:49:83:e8:95:4f:d9:6a:
b0:fb:f6:71:09:06:9f:f8:99:8f:cf:dc:d7:ff:aa:
f6:cb:c5:69:07:56:fd:c3:5a:44:8d:04:d4:98:08:
7d:c9:ec:5e:5a:21:97:f9:dd:3f:5e:f9:0e:fa:90:
05:08:1f:29:61:46:26:53:40:22:5e:c5:36:5e:a6:
4c:8f:4f:6b:33:0e:ad:81:a4:24:ad:03:cf:d8:df:
e8:a7:ca:b0:4f:ee:14:df:95:1a:7b:10:b1:8e:7b:
5a:4a:a9:e8:4f:7b:a5:b1:30:7e:69:d9:56:70:8d:
95:3f:ff:8b:83:8d:ec:5b:e4:c8:7b:d1:15:bb:4f:
59:5b:80:41:43:63:a3:96:a4:87:79:5b:56:7d:e5:
70:67:24:ab:82:dc:90:53:b1:6f:0c:a2:5e:32:71:
8d:73:fb:c3:95:ac:75:fb:df:f3:5d:4e:f0:cb:23:
dd:e5
publicExponent: 65537 (0x10001)
privateExponent:
00:bf:98:0a:ce:01:5f:77:e0:97:91:4b:84:5f:09:
c8:24:ce:1c:b3:3d:71:aa:7d:7c:94:ec:e9:c2:71:
f5:ab:08:e6:db:b4:b6:1f:14:72:59:60:9d:47:f2:
64:2e:e2:db:57:fd:4a:51:2e:6f:c0:ee:3f:9a:a2:
6b:02:7e:98:de:33:e5:e0:81:40:8e:8a:ec:6c:fd:
ce:59:ea:69:91:a1:a3:03:7f:06:96:77:ed:8a:d0:
a1:e1:c8:a0:be:e0:f8:ff:be:9f:f2:01:b5:00:42:
cd:b4:c2:ad:20:a6:22:5b:b0:4f:72:ca:1f:13:d4:
61:b7:05:0e:35:c7:3f:97:c9:3e:b7:42:7c:ce:dd:
c2:b3:61:ad:43:42:00:e6:3a:6d:c8:19:4d:9d:77:
de:1d:2e:8a:da:56:a7:6c:ef:ff:ae:32:5c:b9:ba:
4f:7c:df:b5:9d:7e:2d:bc:8c:7e:31:c6:5f:7f:dc:
c9:88:75:59:ac:17:c7:31:db:06:f2:46:7f:ff:e2:
b5:7b:1f:f6:27:5b:fd:81:d3:79:4a:b4:7e:10:61:
eb:35:5e:0b:b1:b7:8a:52:61:b9:d2:9b:df:9c:ca:
84:42:d6:f9:64:e4:6d:ef:dd:32:55:a4:a7:f8:4f:
56:41:18:db:e7:88:bd:5c:97:34:c1:30:3f:01:4d:
0a:01
prime1:
00:f6:b9:66:50:ac:c7:82:5a:b5:39:1b:ea:ce:58:
05:35:43:7a:6d:c2:2d:5c:fc:ea:96:59:52:64:86:
08:f9:91:c7:8e:ca:cf:d3:37:fe:d8:c3:49:e6:f0:
81:92:c0:ff:91:16:49:a2:79:6d:b6:18:95:25:2d:
b7:39:04:49:c0:c8:4d:15:0a:ea:5f:1c:b0:ad:47:
83:6b:01:fc:e3:3d:50:4d:61:ad:48:2b:8c:bd:23:
68:1f:17:88:41:26:a6:1b:84:2a:f9:a9:f6:47:92:
60:7c:ed:e1:f9:d4:af:a5:da:df:5f:89:a6:43:8a:
3a:2b:5f:d0:e7:b6:3e:99:b1
prime2:
00:ea:28:7e:71:84:19:a0:d1:64:57:3c:b5:d5:e6:
90:c7:eb:39:9a:d3:e1:4e:96:46:2b:90:f5:83:74:
4d:68:95:8a:04:1e:68:f8:37:01:50:08:f6:22:d7:
95:1e:63:e0:d4:2c:ae:61:67:99:e6:4f:42:ba:54:
dd:4f:c9:fc:28:6b:19:f0:26:8e:27:d7:3a:b7:6a:
49:2a:fb:ce:ee:1e:00:3e:b3:5e:23:ae:5e:97:c8:
51:4b:9d:76:d5:08:b9:dc:5a:37:f4:57:74:a5:0c:
cb:8b:14:d1:68:8a:1d:44:d4:b5:0c:2f:30:fb:77:
09:8f:c8:51:88:9d:49:a0:75
exponent1:
00:f3:30:6f:cf:59:5f:15:f7:fe:e5:19:c5:6a:3a:
8c:77:a1:d9:8d:52:76:90:4f:a3:93:2a:db:f1:c5:
c4:16:eb:40:7e:59:1e:5c:9d:b7:0f:45:ff:14:29:
40:2e:bd:19:ab:93:02:65:a9:b7:20:64:3e:ae:74:
cf:42:de:1d:2c:6e:c2:bb:d9:14:87:47:aa:46:42:
55:21:26:c6:73:de:3d:c6:e8:5e:7a:e2:a2:48:d4:
1b:8f:7a:0c:8d:db:60:a3:82:b5:31:7d:fc:09:34:
18:f3:4b:2f:10:a8:39:b2:0b:79:5d:9c:3a:4c:1c:
75:95:c7:4e:0c:f7:2f:e1:21
exponent2:
5c:ba:56:80:5b:a0:ce:87:bd:65:b2:9c:0b:ad:f7:
cd:c3:c0:17:29:2b:03:35:0d:6a:b9:48:10:9b:a0:
ff:f6:a0:26:4b:68:a4:4b:1c:10:f6:cb:8a:36:b7:
4d:c6:9d:c5:48:40:72:40:55:b8:d7:d0:83:fb:91:
7c:c4:6f:40:0e:51:c2:41:72:70:22:92:95:09:d9:
19:d5:88:37:d1:d7:a4:fc:e1:1d:de:32:85:87:05:
72:9d:53:ee:bf:3a:e3:21:33:21:66:f4:c1:5b:d4:
cb:2a:1e:57:78:c2:68:7c:97:89:d0:b2:64:12:da:
cd:7e:b5:93:15:3e:8f:f5
coefficient:
10:51:47:1e:6c:f0:64:42:53:a7:9d:62:31:06:e4:
53:73:ab:8b:06:ce:90:2e:22:6c:e1:3b:c8:2a:69:
34:58:d2:d9:10:c8:81:76:41:c6:77:89:33:32:61:
d1:6f:3f:17:8e:d2:c4:31:14:5f:b1:92:84:76:7f:
45:a6:34:7e:ad:cd:36:40:15:3a:07:37:43:a5:48:
fa:81:32:70:69:77:84:79:1a:f3:ab:e0:a9:41:b5:
7a:e3:f9:32:dc:d6:ae:1c:8b:66:da:9c:59:64:92:
d4:4e:a8:dc:0b:b9:a3:a0:21:29:26:1c:a1:dc:e6:
85:57:3c:62:74:96:4c:d4
The remedy would be to
The remedy would be to generate a self-signed cert on the box, and trust that one.
nvm, they just changed that:
For security reasons, the default CA certificate used in HTTPS scanning in your appliance has been replaced with a unique CA certificate. For uninterrupted secure browsing over HTTPS, you may need to re-import the same in the browser. For more information, click here:
http://kb.cyberoam.com/default.asp?id=2339&Lang=1&SID=
Just FYI: there appear to be
Just FYI: there appear to be no Cyberoam certificates of any kind installed by default in OS X 10.7 "Lion".
Cyberoam_SSL_CA.pem =========
Cyberoam_SSL_CA.pem
=====================
-----BEGIN CERTIFICATE-----
MIIFADCCA+igAwIBAgIJAKa1LpKB0iJiMA0GCSqGSIb3DQEBBQUAMIGwMQswCQYD
VQQGEwJJTjEQMA4GA1UECBMHR3VqYXJhdDESMBAGA1UEBxMJQWhtZWRhYmFkMRIw
EAYDVQQKEwlFbGl0ZWNvcmUxJzAlBgNVBAsTHkN5YmVyb2FtIENlcnRpZmljYXRl
IEF1dGhvcml0eTEYMBYGA1UEAxMPQ3liZXJvYW0gU1NMIENBMSQwIgYJKoZIhvcN
AQkBFhVzdXBwb3J0QGVsaXRlY29yZS5jb20wHhcNMTAwNTEwMDc1NjA0WhcNMzYx
MjMxMDc1NjA0WjCBsDELMAkGA1UEBhMCSU4xEDAOBgNVBAgTB0d1amFyYXQxEjAQ
BgNVBAcTCUFobWVkYWJhZDESMBAGA1UEChMJRWxpdGVjb3JlMScwJQYDVQQLEx5D
eWJlcm9hbSBDZXJ0aWZpY2F0ZSBBdXRob3JpdHkxGDAWBgNVBAMTD0N5YmVyb2Ft
IFNTTCBDQTEkMCIGCSqGSIb3DQEJARYVc3VwcG9ydEBlbGl0ZWNvcmUuY29tMIIB
IjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA4ax+WmILhtQDBuW1VAY3gAKo
OBGLD34GyKXHBKepRDLgn7n/3sYuXj4D8Og9sjhdBuw+o+jji2IFtZVbMjas6NU2
BIX8dynmtmTn//d6ACALXEmD6JVP2Wqw+/ZxCQaf+JmPz9zX/6r2y8VpB1b9w1pE
jQTUmAh9yexeWiGX+d0/XvkO+pAFCB8pYUYmU0AiXsU2XqZMj09rMw6tgaQkrQPP
2N/op8qwT+4U35UaexCxjntaSqnoT3ulsTB+adlWcI2VP/+Lg43sW+TIe9EVu09Z
W4BBQ2OjlqSHeVtWfeVwZySrgtyQU7FvDKJeMnGNc/vDlax1+9/zXU7wyyPd5QID
AQABo4IBGTCCARUwHQYDVR0OBBYEFMaO7snsjSZzegkSuHPxvq+3ZYjhMIHlBgNV
HSMEgd0wgdqAFMaO7snsjSZzegkSuHPxvq+3ZYjhoYG2pIGzMIGwMQswCQYDVQQG
EwJJTjEQMA4GA1UECBMHR3VqYXJhdDESMBAGA1UEBxMJQWhtZWRhYmFkMRIwEAYD
VQQKEwlFbGl0ZWNvcmUxJzAlBgNVBAsTHkN5YmVyb2FtIENlcnRpZmljYXRlIEF1
dGhvcml0eTEYMBYGA1UEAxMPQ3liZXJvYW0gU1NMIENBMSQwIgYJKoZIhvcNAQkB
FhVzdXBwb3J0QGVsaXRlY29yZS5jb22CCQCmtS6SgdIiYjAMBgNVHRMEBTADAQH/
MA0GCSqGSIb3DQEBBQUAA4IBAQC3Q8fUg8iAUL2Q01o6GXjThzSI1C95qJK3FAlG
q/XZzhJlJfxHa3rslcDrbNkAdKCnthpF07xYBbAvh0cIn0ST98/2sHJDJ4sg3Pqp
HUtNOL3PpNMgdqXtoQgKcm8XtkBOppGrCR4HTcRjf0ZLfWP71S3/Ne1o1U10KrPh
LWGYME+4Uh6lo7OBdZp8C8IjPYT2GSCquh/wWrtSYspfO4HJw/5dXaY7wfTh8P0k
/ENLBUUzENiiDiyhXKEZvCAbX+KWNq2T4w7r+411ycV828cuwZx/MehWQrw2SpjC
3sVdb7GwxgxcyGE6TM39Ht3Jl4scTFmKZrG8A9BwTYQsvm6I
-----END CERTIFICATE-----
ze press is watching you
ze press is watching you blog:
http://www.h-online.com/security/news/item/Cyberoam-appliances-private-…
thanks for not approving my
thanks for not approving my post but instead approving others. FU!
http://blog.cyberoam.com/2012
http://blog.cyberoam.com/2012/07/cyberoam%E2%80%99s-proactive-steps-in-…
http://mashable.com/2012/07/1
http://mashable.com/2012/07/12/facebook-scanning-chats/
runa, take your fight with this now....
I think it's rather
I think it's rather difficult to argue against it as use of Facebook implies consent to its use of whatever data it maintains about its visitors as it pleases. Whilst I agree that it demonstrates another gross abuse of its visitors, it isn't unexpected, Mark Zuckerberg's dislike of Facebook's visitors is already known about. He isn't to be trusted. I'd suggest using Cryptocat, as it's safer, but not safe.
https://src.chromium.org/view
https://src.chromium.org/viewvc/chrome/trunk/src/net/base/cert_verify_p…
Goodnight sweet prince
Thank you for making the
Thank you for making the sincere attempt to speak about this on blog.torproject.org . I feel very strong about it and would like to read more. If it's OK, as you achieve extra extensive wisdom, may you mind including extra articles similar to this one with additional info? It will be extraordinarily useful and helpful for me and my friends. Great!
blog.torproject.org is a one
blog.torproject.org is a one of the more impressive phorums I've seen. Thanks so much for keeping the internet classy for a change. Youve got style, class, bravado. I mean it. Please keep it up because without the internet is definitely lacking in intelligence. Wonderful!
blog.torproject.org is
blog.torproject.org is wonderful. There's always all of the ideal info in the ideas of my fingers. Thanks and keep up the excellent work! Wonderful!
perfect design on
perfect design on blog.torproject.org thanks Wonderful!